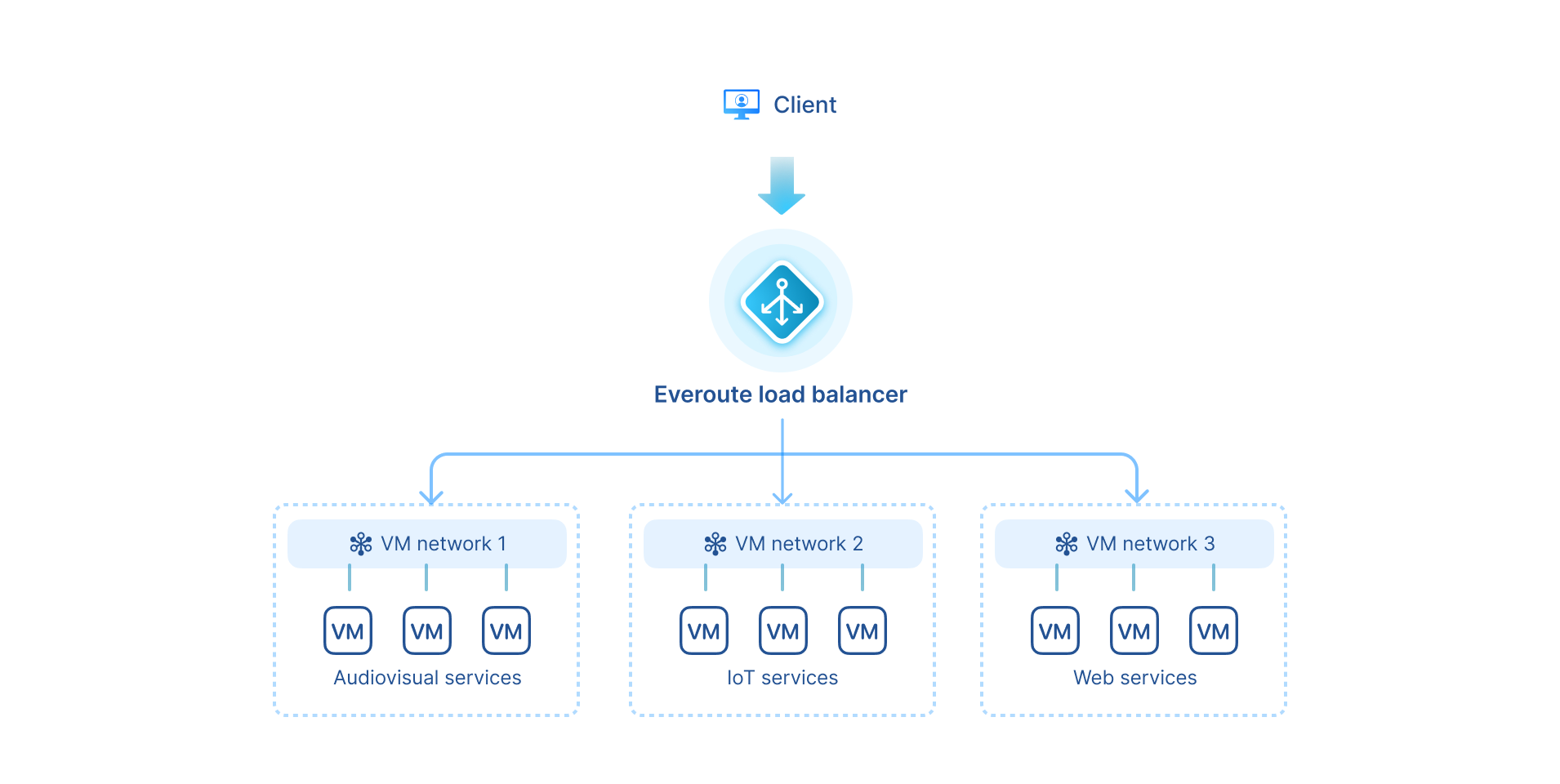
Everoute provides software-defined network and security capabilities. It offers functionalities such as the distributed firewall, network load balancer, virtual private cloud (VPC) networking, and container network, and supports both virtualized and containerized apps, forming a unified network and security solution.
跳转到您所在的国家或地区
我们建议您访问当前所在地的网站,了解针对您所在的国家或地区提供的产品与服务。
我们根据 IP 地址判断大致位置。若您正通过代理服务器访问,则位置可能与实际不同。隐私政策
留在 HK & Macao (English) 站点