In recent years, more and more organizations have regarded ransomware attacks as a vital threat. This is because, besides the potential data loss and ransom payment, as Gartner mentions*, the real threat is “the impact on the business from the sudden elimination or interruption of services or processes.”
To help customers defend against ransomware attacks, SmartX has introduced HCI 5.1 portfolio with upgraded anti-ransomware capabilities. Leveraging SmartX observability platform (based on CloudTower), software-defined network and security product – Everoute, and SMTX Backup & DR, organizations can protect their systems from ransomware through a three-stage strategy: actively detect ransomware attacks, isolate infected VMs, and recover data in a secure environment.
Three-stage Strategy: Detect, Isolate, and Recover
Unlike any other cyber crimes, with ransomware, hackers encrypt enterprises’ critical data, which is difficult to crack even for professional network security engineers. This means that to effectively defend against ransomware attacks, organizations need to prevent ransomware intrusion and lateral movement before hackers implement encryption, or to minimize losses of any data that may have already been encrypted.
In virtualization/HCI environments, there is a large number of VMs that migrate frequently, making it difficult to protect the entire environment only with traditional “north-south” firewalls and network security products for malware detection and removal. Therefore, as Gartner emphasized in “How to Prepare for Ransomware Attacks”, ransomware prevention goes far beyond just the endpoints, and organizations must implement comprehensive solutions across applications and IT infrastructure to address the various stages of ransomware attacks.
In the table below, we clarify three major stages of ransomware attacks and highlight their characteristics. In general, to effectively prevent ransomware from intrusion, lateral movement, and attack, enterprises should adopt IT infrastructure solutions that support rapid ransomware detection, effective lateral movement of VMs, and secure data recovery.
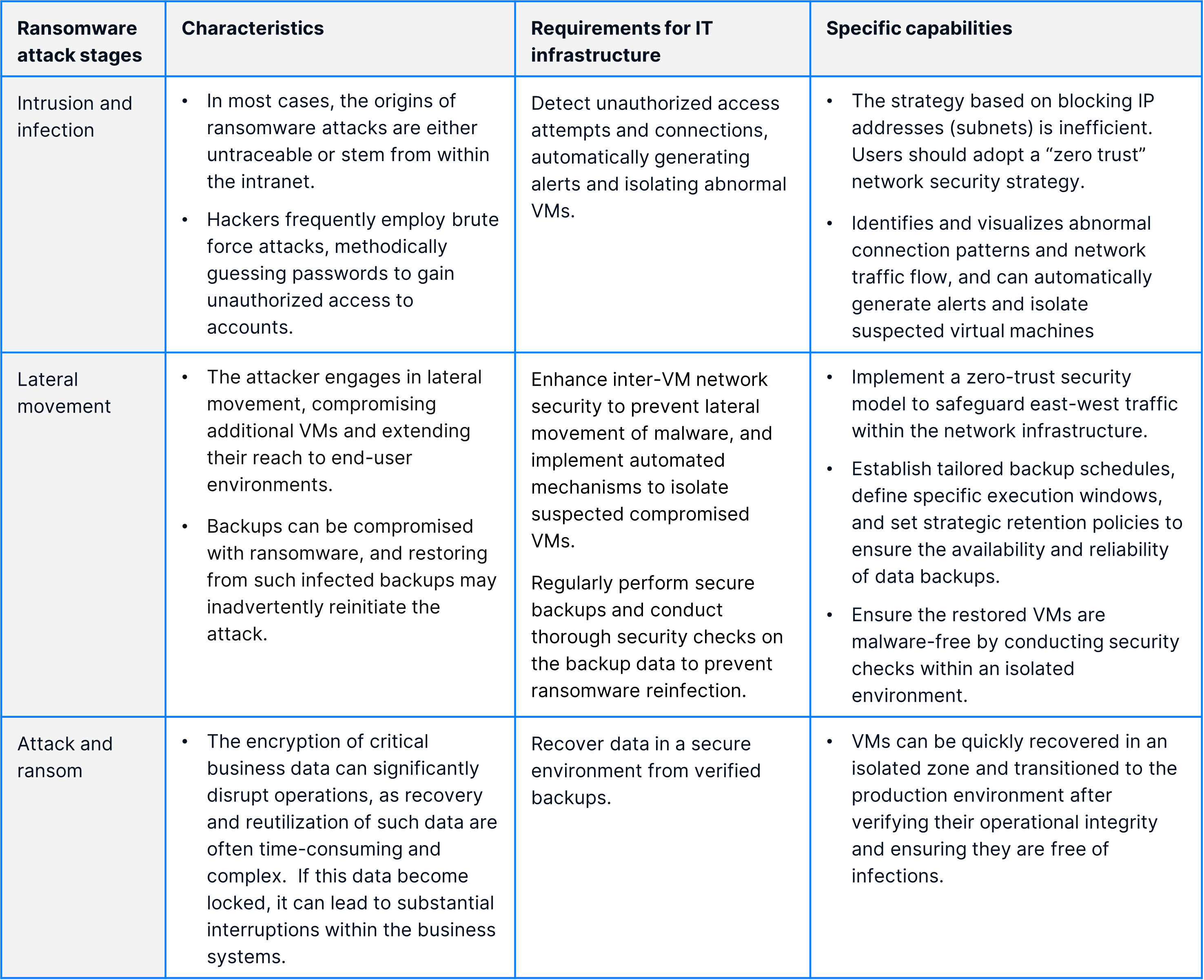
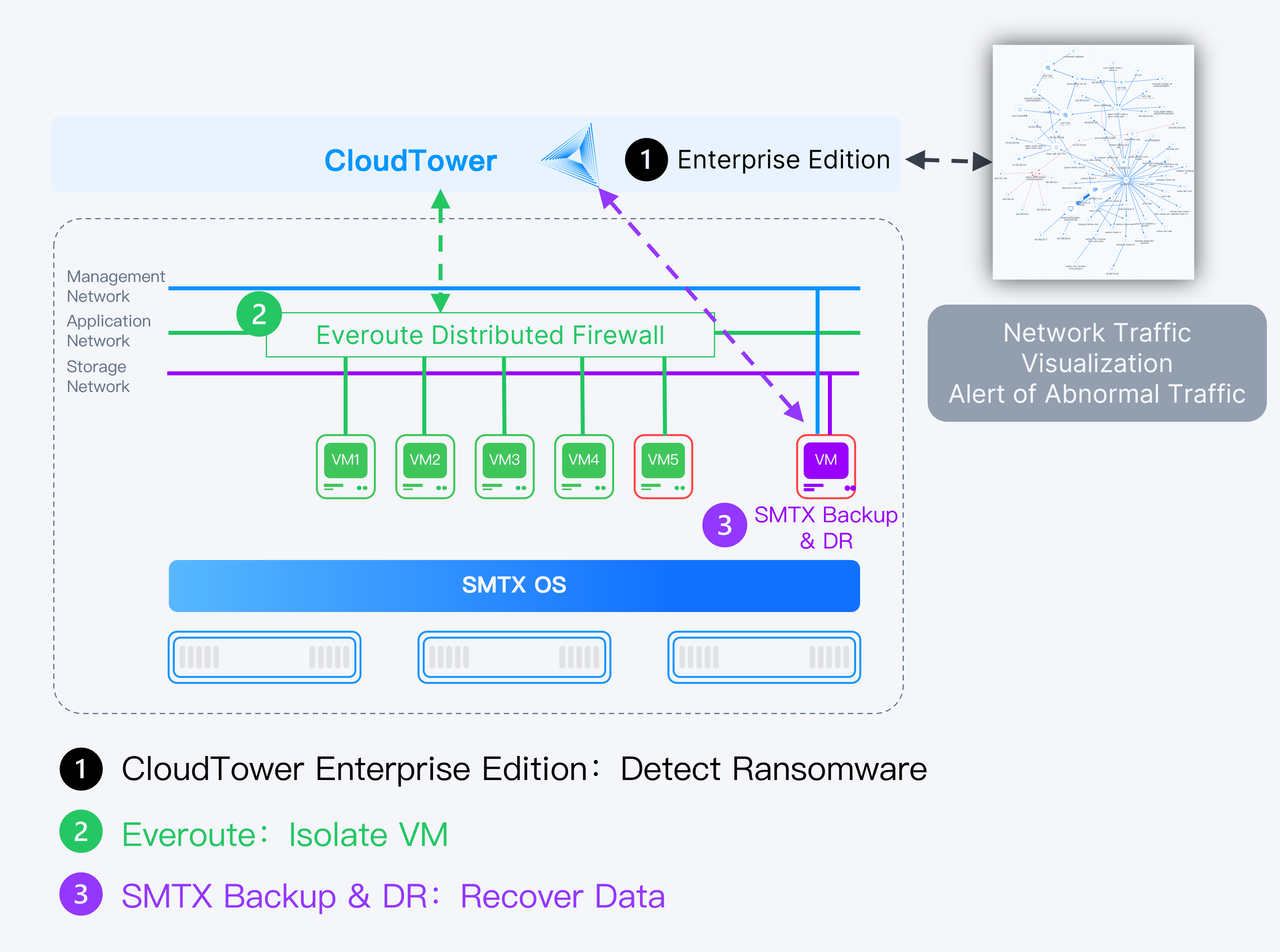
Defend Against Ransomware with SmartX HCI
With the Network Traffic Visualization feature, Everoute distributed firewall, and SMTX Backup & DR, users can significantly enhance the anti-ransomware defenses of their HCI system.
Network Traffic Visualization: Proactively Alert Abnormal Traffic and Quickly Identify Ransomware Attacks
Network Traffic Visualization is a key feature of SmartX’s Observability platform (based on CloudTower). It can visualize VM-VM, VM-host, and host-host network in the cluster, along with other relevant information, allowing O&M engineers to gain a comprehensive understanding of virtual network traffic status.
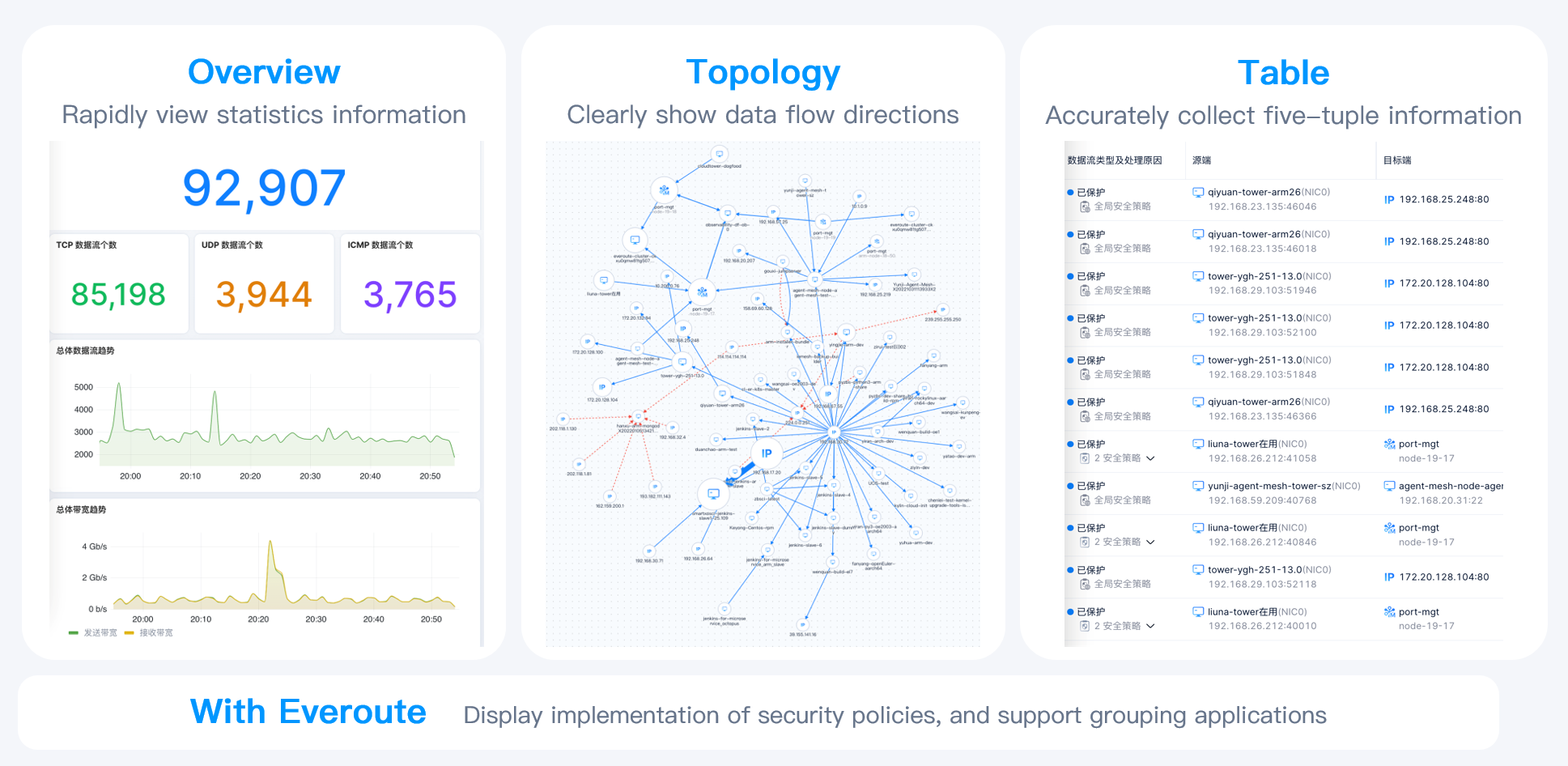
If hackers intrude with brute-force attack, the number of connections will surge in a short period. With CloudTower Enterprise Edition, administrators can set the threshold for the number of connections to VMs. Once the number exceeds the threshold, it will automatically trigger an alert, allowing administrators to pinpoint which VM is experiencing unusual connections through the network traffic visualization interface. In conjunction with Everoute, suspicious VMs can be further isolated and their traffic will be blocked. At this time, administrators are allowed to check the VM status and recover data.
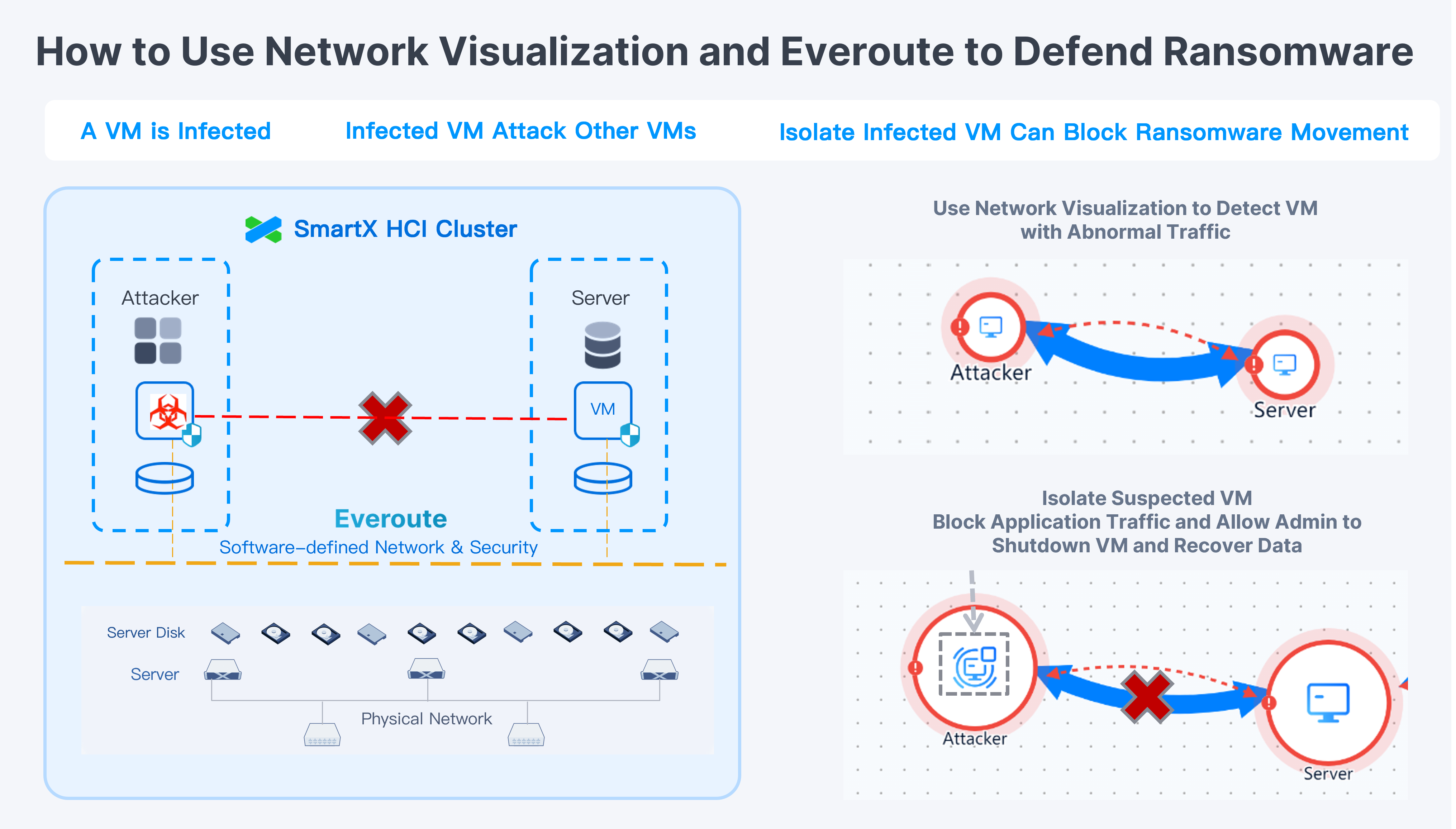
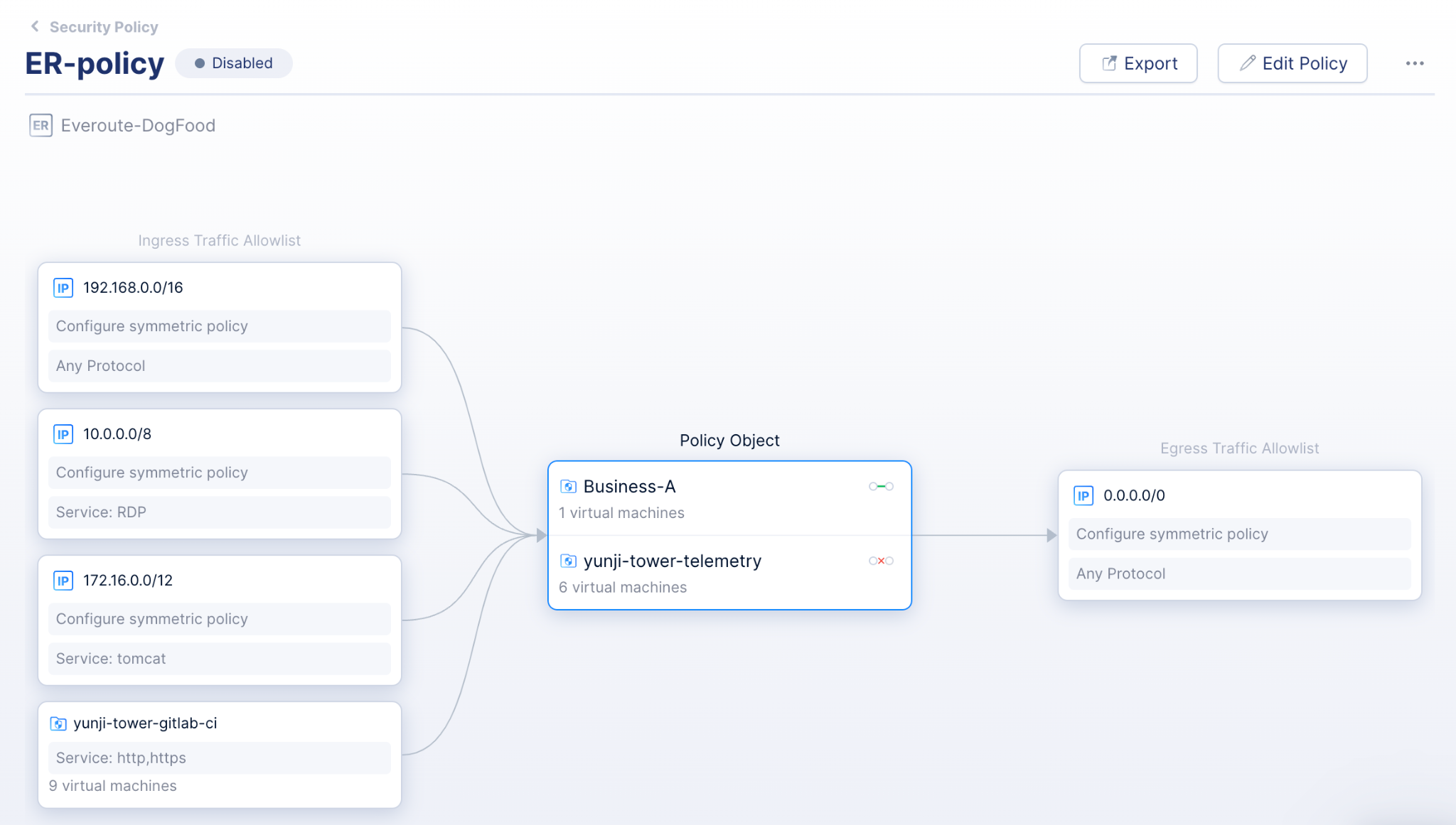
Everoute Distributed Firewall: Isolate Suspicious VMs with One-click and Prevent Lateral Movement of Ransomware
Featuring whitelist-based security policies and sticky policies, Everoute implements a micro-segmented network model adhering to the zero trust principle, and extends multiple distributed firewall policies to safeguard individual virtual machines from cybersecurity threats.
- Whitelist-based security policies: Whitelist-based security policies ensure that east-west access between virtual machines conforms to the “least privilege” principle.
- One-click isolation of suspected VMs: Isolate suspected and infected VMs with one click, and set dedicated access policies for them in order to process further operations such as shutdown and recovery.
- VM labels and security groups: Tag virtual machines with “labels” and “security groups” to provide a clear view of security policies. VMs can be dynamically assigned to “security groups” based on label or label combinations, simplifying security policies for non-contiguous IP addresses.
- Sticky policies: Security policies can follow virtual machines as they migrate automatically from host to host, cluster to cluster, without the need to reset them. Security policies are enforced independent of physical host, segment, and IP address of the virtual machine.
- Visualize VM traffic and the execution of security policies: Collaboratively using Network Traffic Visualization and Everoute, users can monitor the implementation of security policies, ensuring the effect of security policies meets their expectations.
Moreover, with the Everoute Container Plugin, users can extend distributed firewall capabilities to containers managed by the SMTX Kubernetes Service, enabling flat container network connectivity and network policies (Kubernetes Network Policy).
SMTX Backup & DR: Secure Data Recovery and Maintain Production Stability
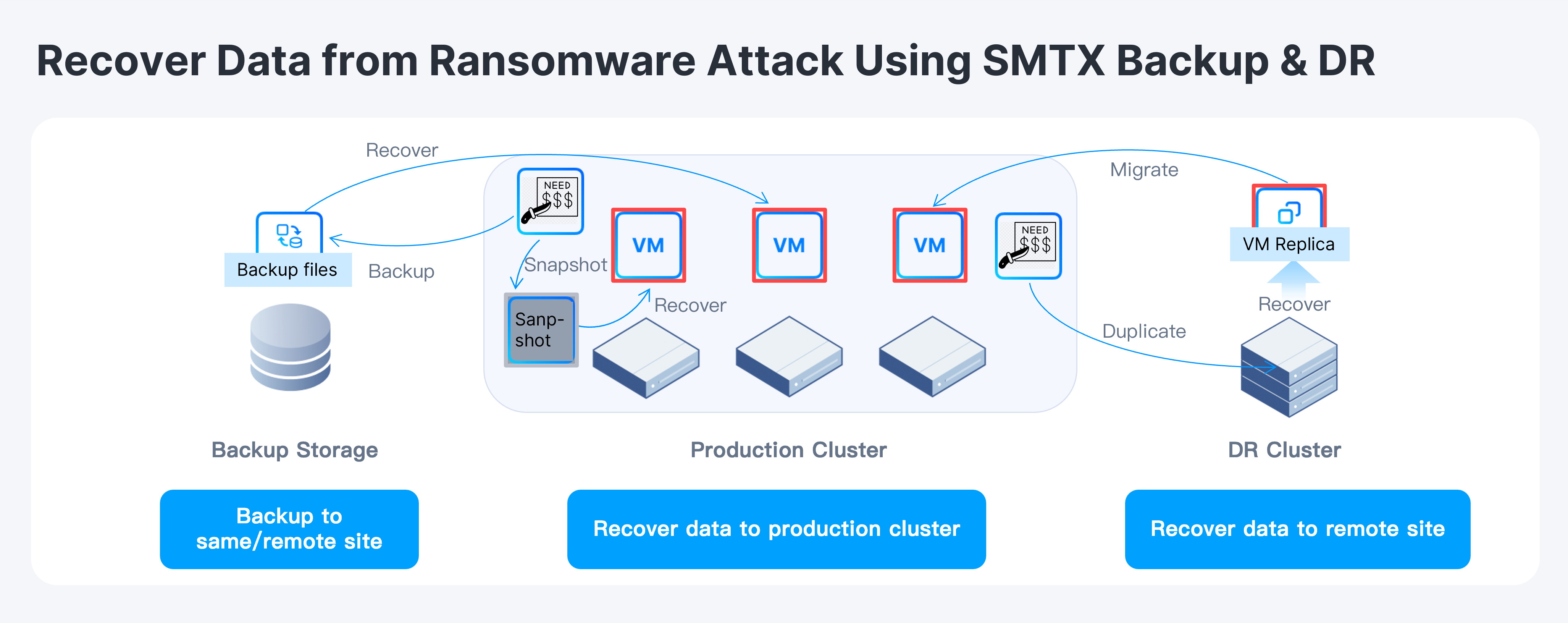
SMTX Backup & DR integrates the original SMTX Backup & Recovery with the asynchronous replication capabilities built into SMTX OS, to provide a comprehensive data protection and disaster recovery solution for virtual machines running on SMTX OS (ELF) clusters.
Administrators can back up VM data from the HCI environment to external NAS storage with SMTX Backup & DR, which allow admins to customize backup schedules, execution windows, and retention policies. Once the criminal implements the ransomware attack, admins can recover/rebuild VMs from time-stamped local snapshots that capture specific states at scheduled intervals, and use Everoute’s “one-click isolation” feature to place the recovered VM in an isolated state. Once the VM is cleaned and verified, it will be released and put into the production environment.
Alternatively, users can choose to rebuild VMs in a remote site and put them into the production environment either in the remote or original site after being cleaned and checked in an isolated state.
Advantages of SmartX HCI’s Three-stage Strategy
- Agentless: Eliminates the need for intrusive operations on Guest VMs, ensuring uninterrupted business services.
- Ease of O&M: Simplify operations and maintenance by configuring and managing all three components via CloudTower’s unified interface.
- No dependency: Components are independently operable, yet when used collaboratively, they provide an enhanced ransomware defense strategy.
For more information on SmartX HCI and its anti-ransomware capabilities, please refer to our previous blogs:
Eliminate Virtual Network Blind Spots with SmartX Network Visualization
SmartX HCI 5.1: Enhanced Features and New Components
Reference
Quick Answer: What Happens If You Pay the Ransomware Demand?
https://www.gartner.com/document/4970531
Ransomware Recovery Requires a Layered Recovery Response
